Process Flow Diagrams Are Used by Which Threat Model
Analysis of actions taken. This information is documented in a resulting Threat Model document.
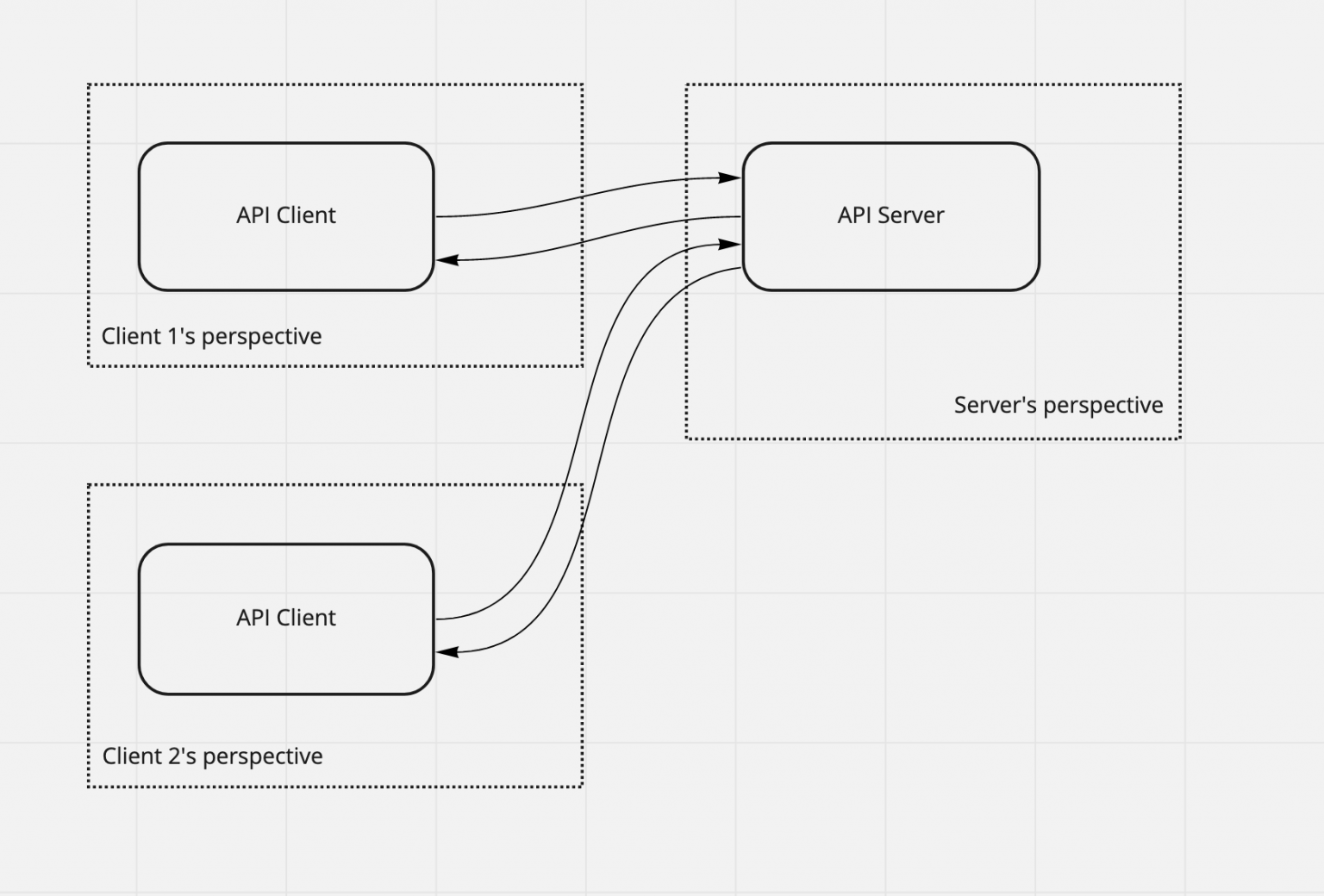
Shostack Associates Shostack Friends Blog Threat Model Thursday Data Flow Diagrams
The flow diagram are created with the python threat modeling framework pytm with diagrams generated as Dot and PlantUML.
. 1Application Threat Models 2Operational Threat Models. These were specifically designed to illustrate how the attacker thinks. Data flow diagrams therefore are generated as a means of communicating this to the outside world those who are not threat modelers.
Visual Representation using Process Flow Diagram To deal with the limitations of DFD based threat modelling Process Flow Diagrams were introduced in 2011 as a tool to allow Agile software development teams to create threat models based on the application design process. Determine and Rank Threats. A Threat model is encapsulated in a Trust diagram a specific version of a Data Flow diagram.
Flow sequence and attack tree diagrams cover the initial steps of an online payment process. Data Flow Diagrams DFDs in the Threat Modeling Arena While DFDs are used to document the flow of data in out and around a system application or process they lack the deeper contextual insights that PFDs offer. It can be done of any time during the life cycle of applicationsystem but will provide a maximum return of design time.
Application threat models use process-flow diagrams representing the architectural point of view. Process Flow Diagrams are used by _____. Data-flow diagrams are graphical representations of your system and should specify each.
Process Flow Diagrams PFDs vs. The attack tree is generated with. Threat modeling process Figure 1 requires a repeatable approach.
An attack tree started with a root node denotes an attackers primary objective and children nodes that branch off it. From the diagram potential threats are identified and for each threat mitigations are proposed. If you would like to know more about process flow architectural diagramming and the ThreatModeler platform please feel free to contact us for a more in.
Application threat models for development teams and operational threat models for the infrastructure teams. ThreatModeler leverages architectural process flow diagrams which are perfect for securing. A list of potential threats.
Q1 The following is a part of a threat model except _________. Mitigation steps for each threat. Application threat models and operational threat models.
Architectural threat models are represented through process-flow diagrams and operational threat models are represented through Data Flow Diagrams. Analysis of actions taken. DATA FLOW DIAGRAMS A Data Flow Diagram DFD for Minesweeper a game that ships with Windows TM is shown in Figure 1.
This methodology utilizes two threat models. Process Flow Diagrams are used by _____. These initial steps cover the payment from the customer - customer client home pc - merchant - stripe.
Operational threat models are created from an attacker point of. Modern fast moving highly agile operational and development environments throughout the SDLC. They genuinely allow incorporation of developers in the threat modeling process during the application design phase.
In some cases the mitigation is a change in the design itself in which case the new or changed elements must be analyzed in an additional iteration. Recognizing differences in operations and concerns among development and infrastructure teams VAST requires creating two types of models. When you encounter a cyber threat in your businesss information technology IT infrastructure you can use the DREAD model to determine how much damage it has already caused and can cause in the future.
To indicate how developers need to address those threats starting with the creation of a process flow diagram PFD. PFDs visually demonstrate the relationships between components and processes providing a view similar to that of an attacker. The PFD allows developers security professionals and other stakeholders to build and modify threat models as functional maps a visual decomposition of an application in accordance with the way developers think about the coding.
We represent a DFD as a runtime view following the Component-and-Connector viewtype 2. This helps developers working within an Agile development methodology initially write secure code. The DFDs show the different paths through the system highlighting the privilege boundaries.
Choose the correct option from below list 1Application Threat Models 2Operational Threat Models. Threat Modeling Interview Question-Answer. Operational threat models are created from an.
The DREAD model is a form of quantitative risk analysis that involves rating the severity of a cyber threat. Create a threat model using data-flow diagram elements. Which of the following security property does Tampering violate.
Process flow diagrams are the result of a maturing threat modeling discipline. It is also used to produce data flow diagrams DFDs for the application. Threat Modeling is one of the disciplines that can lift your risk management program and make it excellent.
VAST requires creating two types of models. Application threat models use process-flow diagrams representing the architectural point of view. Consequently the Data Flow Diagrams DFDs and Process Flow Diagrams PFDs used to model threats and better understand how bad actors can gain access to an asset are significantly more complex than they would be with known.
Our industry has standardized using the term loosely an approach that uses data flow analysis for much of our threat modeling. Application threat models for development teams are created with process flow diagrams PFDa flowchart that helps to describe the general flow of a business process and how the user would interact with. It is useful when we consider the flow of information across our systems.
Application threat models and operational threat models. Process Data store Data flow External Interactor Boundary TRUST LEGEND High Medium Low - Figure 1.

How To Process Flow Diagram For Threat Modeling Threatmodeler
Threat Modeling An Application Moodle Using Stride By Vlad Spades Medium

Figure 1 From Solution Aware Data Flow Diagrams For Security Threat Modeling Semantic Scholar
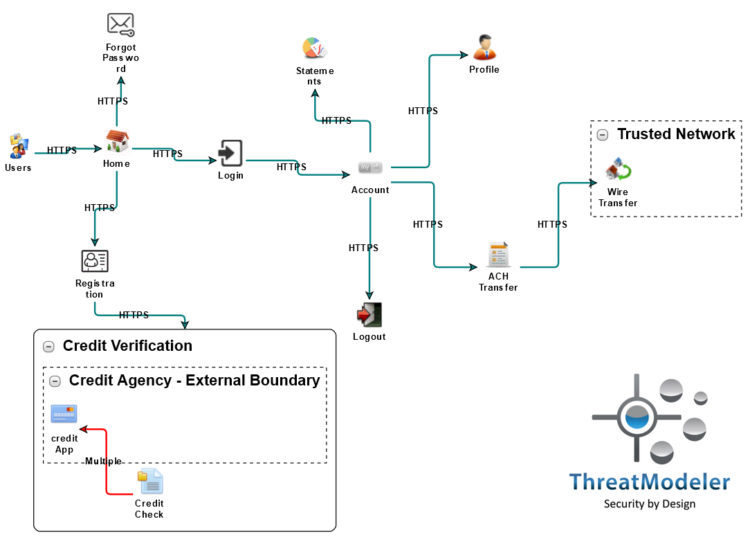
Process Flow Vs Data Flow Diagrams For Threat Modeling

Document Your Privacy Threat Modeling With Owasp Threat Dragon
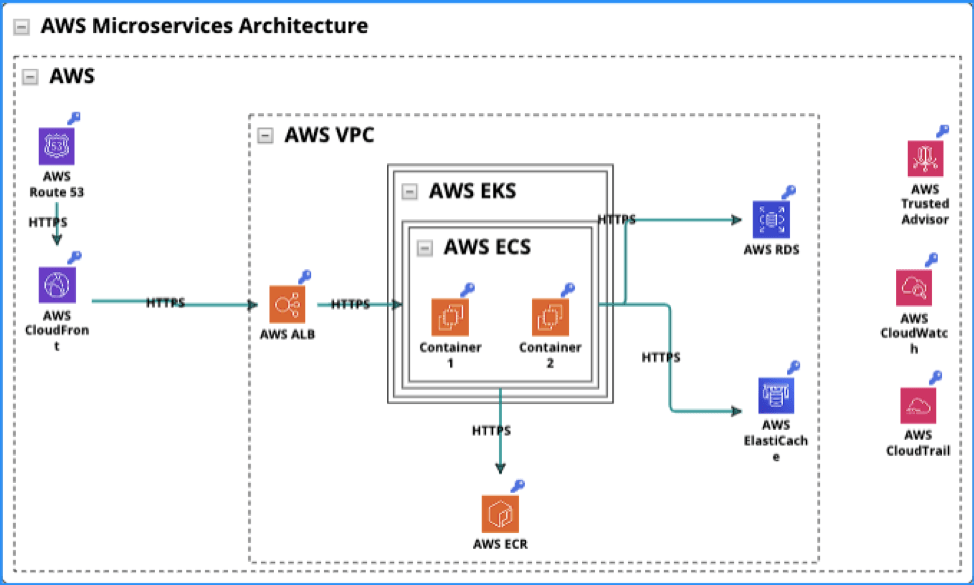
Architecturally Based Process Flow Diagrams Threatmodeler
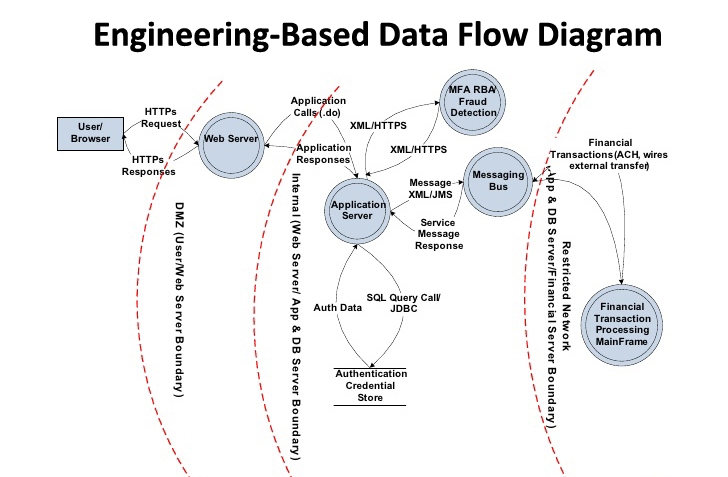
Process Flow Vs Data Flow Diagrams For Threat Modeling
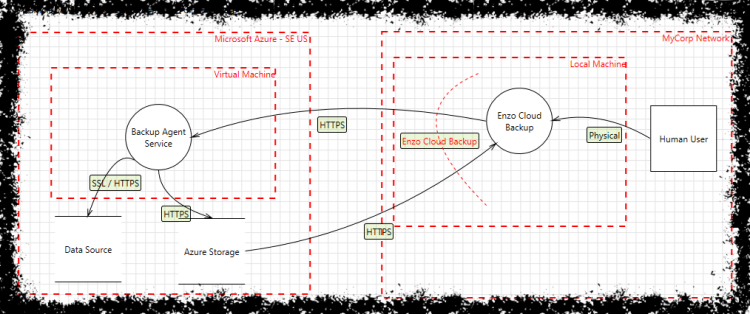
Shostack Associates Shostack Friends Blog Data Flow Diagrams 3 0
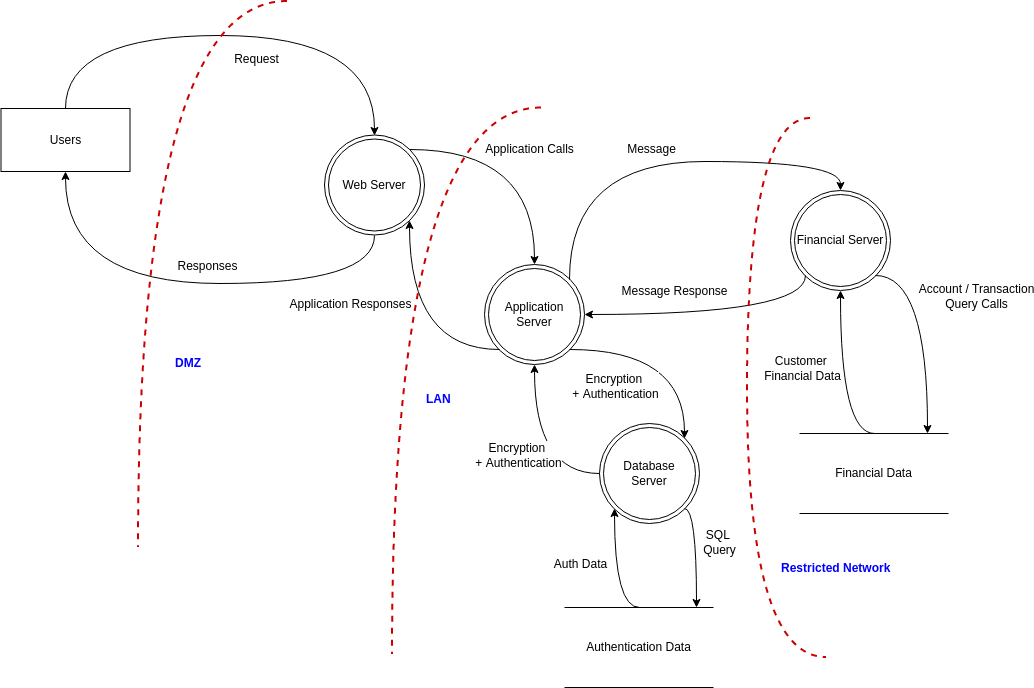
Website Threat Modeling Threat Model Diagram Template
Process Flow Vs Data Flow Diagrams For Threat Modeling
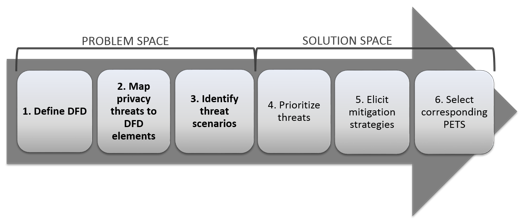
Threat Modeling Process Owasp Foundation

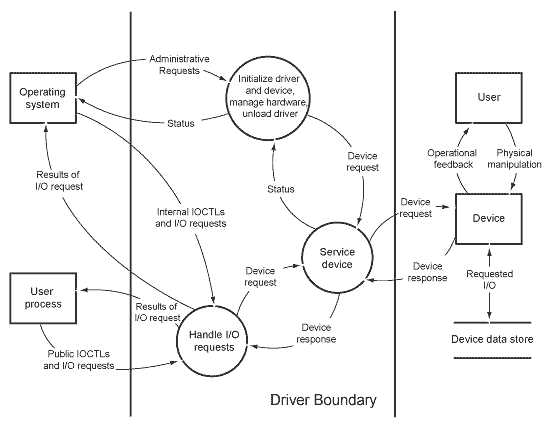
Threat Modeling For Drivers Windows Drivers Microsoft Docs
Threat Modeling 12 Available Methods
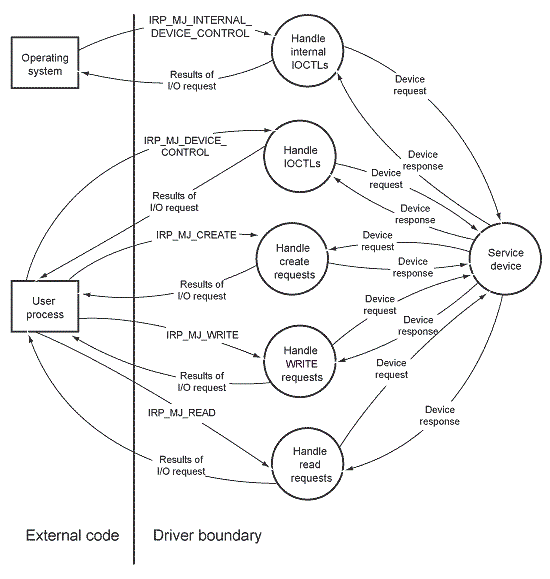
Threat Modeling For Drivers Windows Drivers Microsoft Docs
Threat Modeling Process Owasp Foundation

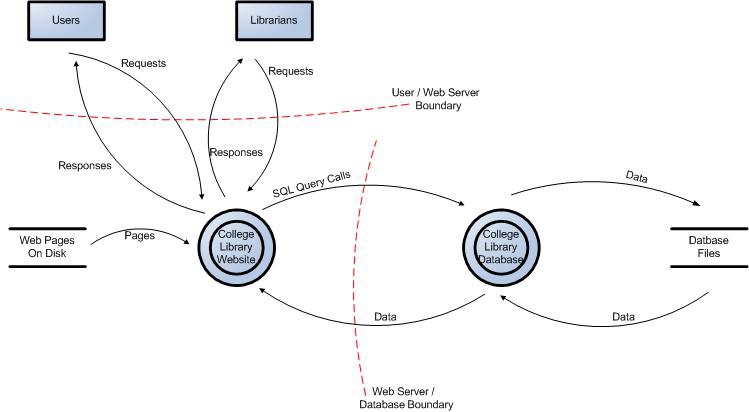
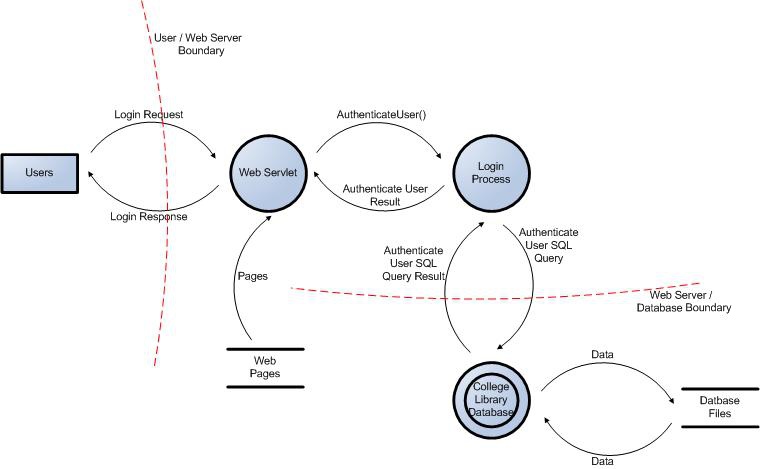
Threat Modeling Dataflow Diagram How Far Do I Need To Drill Down Information Security Stack Exchange

Comments
Post a Comment